
The network you are using is connected to the Internet, protected with a network firewall, a computer that selectively allows connections between internal and external systems. The firewall blocks all traffic between the Internet and the protected network, but permits users on the protected network to carry out certain basic operations. These are:
A number of services are not provided, as there is generally no secure method of providing them. These include talk, rusers, NFS, and many others. The general view is that that which is not specifically allowed, is forbidden. While this may seem like an inconvenience, it is necessary for the survival of our internal systems that we maintain this apparently-paranoid stance.
Additional services may be provided as time goes by.
In order to use the available services, you must be logged into a computer that is running TCP/IP on the protected ("inside") network. Electronic mail requires no extra action on the part of the user other than specifying a proper Internet-style address. For FTP and TELNET, users first connect to a ``proxy'' server running on the firewall, which will in turn connect them to the destination system. For finger, you must use a special form of the finger command. There are proxy forms of several other remote information commands as well.
Note: in the following examples, where the document says gatekeeper.company.com you can usually use a shorter form (such as gw when you are calling from the inside network.
This document was developed at TIS using Microsoft Word, and distributed in PostScript form accompanying the TIS Firewall Toolkit. It was then converted from PostScript to HTML and cleaned up using SoftQuad's HoTMetaL PRO HTML editor. The section on using remote information services through the gateway was added and numerous minor changes made at the same time. Copyright in this document is retained by Trusted Information Systems. Inc.
In order to use a World Wide Web viewer such as Mosaic from inside the firewall, you normally need to inform the viewer that there is a proxy in use. How you do this depends on the viewer. For most viewers, you can set a series of environment variables or X resources. For Macintosh Mosaic and for the X viewer Netscape, you can specify the proxy information from the Preferences menu.
The server name is sqorch or gw, and the port number to use is 8080.
If you are configuring Mosaic from scratch, you also need to specify the name of our Internal home page, so that Mosaic will start off with our Internal home page instead of trying to fetch a default Home Page from the NCSA each time you start it up.
On most systems, this information is already configured, but if you need to configure it, the following sections show how for the X Mosaic, Netscape MS-Windows, and Macintosh systems
You need to set several proxy resources, as shown below. These are stored in /usr/lib/X11/app-defaults/Mosaic or your own X Resources file.
Mosaic*httpProxy: http://sqorch.sq.com:8080/ Mosaic*ftpProxy: http://sqorch.sq.com:8080/ Mosaic*gopherProxy: http://sqorch.sq.com:8080/ Mosaic*telnetProxy: http://sqorch.sq.com:8080/ Mosaic*homeDocument: http://sqrex.sq.com/HomePage.html
Netscape can be configured from the Options->Preferences dialog. It should look something like this:

There should already be a mosaic.ini file in your Windows directory. Add the paragraph shown below, and re-start Mosaic.
[proxy information] http_proxy=http://sqorch.sq.com:8080/ ftp_proxy=http://sqorch.sq.com:8080/ gopher_proxy=http://sqorch.sq.com:8080/ wais_proxy=http://sqorch.sq.com:8080/
Mosaic is installed and configured on most of the Macintoshes. If you need to configure it, open the Preferences dialog, select Gates, and ensure that you have selected CERN Proxy with the above information. It should look like this:
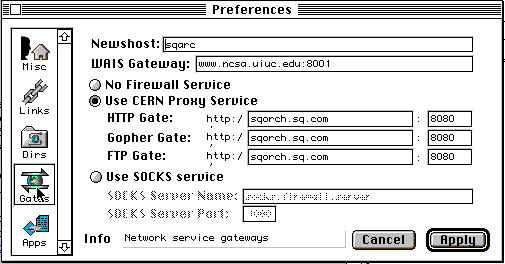
If you have problems, Mosaic for Macintosh is installed and running on the Macs in R & D, and in the Demo area from whence you can copy the information you need.
When connecting to the FTP proxy, you issue the command as if you wished to FTP files with the firewall system itself:
sqhost% ftp gw.sq.comOnce you are connected to the FTP proxy, and you are prompted for your username, give the username and hostname of the system you wish to transfer files with, in the form of username@hostname. If you only have, or prefer to use, the IP network address, you can use username@IP-address . For example, if you wish to log in as
anonymous on the Internet node Ftp.Uu.Net , give your username as anonymous@ftp.uu.netsqhost% ftp gatekeeper.company.com Connected to gatekeeper.company.com 220 gatekeeper FTP proxy (Version 1.0 stable) ready. Name (gatekeeper:you): anonymous@ftp.uu.net 331-(----GATEWAY CONNECTED TO ftp.uu.net----) 331-(220 ftp.uu.net FTP server (SunOS 4.1) ready.) Version Dated: 02/08/94 331 Guest login ok, send ident as password. Password: ###### 230 Guest login ok, access restrictions apply. ftp> dir 200 PORT command successful. (...etc.)
Once you are connected via the proxy and you see the ``GATEWAY CONNECTED TO'' message, any subsequent commands you enter are forwarded to the destination system by the proxy. If you type a password incorrectly, after you are connected, you no longer need to use the user@host form, just act as if the proxy is not there. After connecting, any normal FTP commands can be issued. For details on the other options to the version of FTP on your system, consult the manual. If you are using FTP from outside of your security perimeter, you may have to authenticate yourself to the proxy before you are allowed to transfer files. To authenticate, the FTP user command is used twice in sequence:
outside.host%> ftp gatekeeper.company.com Connected to gatekeeper.company.com. 220-Before using the proxy you must first authenticate 220 gatekeeper FTP proxy (Version 1.0 stable) ready. Name (gatekeeper.company.com:you): 331 SNK Challenge "90280": Password:######### 230 User authenticated to proxy ftp> user you@somebox 331-(----GATEWAY CONNECTED TO somebox----) 331-(220 somebox FTP server ready.) 331 Password required for you. Password: ######### 230 User you logged in. ftp
The first invocation of the ``user'' command (done automatically by the FTP client) authenticates you to the proxy. The second is used to initiate the connection to an FTP server within the security perimeter.
To use the TELNET proxy, simply telnet to the firewall system as if you wished to log into it. There will be a short pause, and you will be prompted with a command prompt for the proxy. At the command prompt, you may specify the host you wish to connect with, by typing
connect hostname or c hostname.If you prefer to give a numeric IP address instead of a host name, you may do so. Once you have entered the name of the host to connect to, the proxy will connect you to that system, and its login prompt should appear. If the system is down or is unreachable, the proxy will inform you of this fact, and you may quit by using the `` quit '' command. For example, if you wish to login to a system named ``Foo.Baz.Com'' you might employ the proxy as follows:
host% telnet gatekeeper.company.com Trying 192.33.112.117 ... Connected to gatekeeper.company.com. Escape character is '^]'. gatekeeper telnet proxy (Version V1.0) ready: tn-gw-> c foo.baz.com HP-UX foo A.09.01 A 9000/710 (ttys1) login: you Password: ###### Please wait...checking for disk quotas unknown mode: crt foo-> (...etc.)
When you logout from the destination system, the proxy will automatically disconnect you and return to a command prompt on your local system.
For communicating with remote systems that support the rlogin protocol, an rlogin proxy is provided. One advantage of the rlogin proxy is that it eliminates the need to authenticate a user twice. In order to use the rlogin proxy, the firewall bastion host must be prepared to accept rlogin connections. If the rlogin proxy is invoked with no user name and destination, it presents the user with a command menu similar to the telnet proxy's:
%-> rlogin gatekeeper rlogin-gw-> ? Valid commands are: (unique abbreviations may be used) connect hostname help/? quit/exit password rlogin-gw-> c somebox.someplace.org Trying you@55.55.55.55... Password: ######## Last login: Mon Oct 25 21:54:33 from homebox.someplace.else SomeOS Release 4.1.Wed Apr 14 07:21:50 EDT 1993 you have new mail somebox%
In this example, the rlogin server on somebox.someplace.org prompted for a password, since the proxy server gatekeeper was not in the user's .rhosts
file. If a username and hostname is specified, the rlogin proxy will automatically reconnect to the specified remote system. For example:
%-> rlogin gatekeeper -l you@somebox.someplace.org Trying you@55.55.55.55... Last login: Mon Oct 25 21:54:33 from homebox.someplace.else SomeOS Release 4.1.Wed Apr 14 07:21:50 EDT 1993 you have new mail somebox%
If using the rlogin proxy from outside the perimeter, it may stop and require authentication before proceeding:
%-> rlogin gatekeeper.your.org -l you@homebox Username: you SNK Challenge "32015": 32256239 Login Accepted Trying you@32.33.22.11... Last login: Mon Oct 25 21:23:53 from some.place SomeOS Release 4.1.3 (homebox) #3: Mon Jun 21 You have new mail. homebox->
Note that some networks block rlogin protocol traffic in or out in such a manner than the rlogin proxy may not be useable. In such circumstances, rely on the telnet proxy instead.
Users who rely on authentication protocols that have passwords or changeable PINs may reset their passwords using built-in capabilities in the proxies. Both the telnet and rlogin proxies support changing passwords at the command line, if connected to from systems within the security perimeter. To change your password, connect to the proxy and issue the "password" command as in this example:
% telnet gatekeeper.your.org Trying 192.33.112.117 ... Connected to gatekeeper. Escape character is '^]'. otter telnet proxy (Version V1.0) ready: tn-gw-> pass Changing passwords Enter Username: you Skey Challenge "s/key 665 ot572005": JAR ADA ANA DRUM GLEN GAUR New Password: ##### Repeat New Password: ##### ID mjr s/key is 666 ot572006 tn-gw-> quit Disconnecting... Connection closed by foreign host. %
In the example above, the user resets their S/Key secret key using the telnet proxy. It is important to remember never to reset the password from a system that may be compromised, or a system that is on an untrusted network. The firewall administrator has the ability to limit the hosts from which users may change their passwords. If you attempt to change your password and cannot, contact your administrator to find out from what hosts password changing is permitted.
On our system, you can run an X application on the outside Internet and display its X window on your desktop (assuming, of course, that you run X on your desktop; almost all operating systems are now X-capable, but you may need to install the X Window System if it isn't already installed).
You can run any X client remotely - even your window manager, if you are the patient sort. However, the X protocol is not very compact, so anything that tries to pick fonts, display fancy graphics, or to very much of anything will take a lot longer than it would locally. However the capability can be invaluable.
The steps are as follows:
$ telnet gw tn-gw-> ? Valid commands are: (unique abbreviations may be used) connect hostname [serv/port] telnet hostname [serv/port] x-gw [hostname/display] help/? quit/exit password tn-gw-> x-gw 192.31.6.47:0 tn-gw-> display port=gatekeeper.sq.com:12 tn-gw-> exit Disconnecting... Connection closed by foreign host. $
Note: If you have a shell-access account on the gateway, you can login there and use x-gw directly instead of starting it through the proxy as shown here.
After the x-gw command, a second pop-up window will appear, with two lines:
Display port is gatekeeper.sq.com:12 Click the button to exit x-gw
and a button labelled EXIT. If you click this button at any time, the x-gw program running on the firewall will terminate, and all your remote X sessions using this connection (if any) will be killed off.
Once the popup appears, you can either exit from the firewall proxy (as shown in this example) or connect to the remote (outside network) machine where the X client is to run. Or, if it is a user on another network, you need to communicate to them the DISPLAY name ("gatekeeper.sq.com:12" in this example).
% setenv DISPLAY gatekeeper.sq.com:12 # csh users $ export DISPLAY=gatekeeper.sq.com:12 # ksh users $ xwhatever -display gatekeeper.sq.com:12 -geometry 24x80+200+0
Normally you'd set DISPLAY in the environment if you expected to run more than one program during this session, or use -display if you only expected to run one.
To terminate all your remote X sessions, click on EXIT in the original x-gw popup window.
There are several services that can be used to query the state of the network or of hosts on the network.
The command info-gw (which can be emulated by telnetting to the gateway on port 64001) provides this information. It gives you a menu of commands:
$ whi Trying 192.31.6.127 ... Connected to gatekeeper. Escape character is'^]'. Welcome to SoftQuad's internal info server. Enter 'help' for command list sq gateway > help archie program finger user@host host host ping host traceroute host whois name sq gateway > traceroute uunet.ca traceroute to uunet.ca (142.77.1.1), 30 hops max, 40 byte packets 1 sqouter-dmz (192.31.6.129) 4 ms 4 ms 4 ms 2 max1.toronto.uunet.ca (142.77.1.210) 32 ms 32 ms 30 ms 3 uunet.ca (142.77.1.1) 34 ms 37 ms 35 ms sq gateway > host uunet.ca. uunet.ca has address 142.77.1.1 uunet.ca mail is handled by mail.uunet.ca uunet.ca mail is handled by mail2.uunet.ca uunet.ca mail is handled by relay1.uu.net uunet.ca mail is handled by relay2.uu.net sq gateway > finger ian@j-random.com [j-random.com] Login name: ian In real life: Ian Darwin Directory: /home/ian Shell: /bin/csh Last login Tue Aug 9 11:52 on ttyu7 from gatekeeper.sq.com No unread mail No Plan. sq gateway > quit Connection closed by foreign host. $
Here is a brief note on each of the commands:
archie tries to locate programs in public anonymous FTP sites around the Internet.
finger gives you information about a user at a remote host, or all users logged in on a remote host.
host tells you the name server's idea of the host's address
Note that due to a bug in the current version of
host, you need to put a period at the end of a fully-qualified name.
ping checks if a remote host or network is reachable.
traceroute is used to find the exact (and often circuitous) route that IP packets actually take from your host to another.
whois tells you about a person, domain or network that is registered with the InterNic (Internet Network Information Center).
As you might expect, the list of services available in this way will change over time, so it may not be exactly as shown in this list.
For more information on the toolkit itself, see the documentation provided with the TIS Firewall Toolkit, by anonymous FTP from ftp.tis.com.
For information on the various commands available under info-gw, use the normal Unix man command.
For information on firewalls and network security, you can't beat the book Firewalls and Internet Security: Repelling the Wily Hacker, by Cheswick & Bellovin (ISBN 0-201-63357-4), Addison-Wesley, 1994.
If you have additional suggestions or services you would like added, please contact the local System Administrator.